Friends of Technology is an IT base firm which seeks to empower both the youth and adults through ICT
Tuesday, 26 August 2014
Friends of Technology: WhatPulse: Track Your Computer Activity and Usage
Friends of Technology: WhatPulse: Track Your Computer Activity and Usage: I clicked my mouse 360 times and keyboard 488 times in last 16 minutes. Yes I can now track my computer activity, including pressed ke...
WhatPulse: Track Your Computer Activity and Usage
I
clicked my mouse 360 times and keyboard 488 times in last 16 minutes.
Yes I can now track my computer activity, including pressed keys, mouse
clicks, used bandwidth and the uptime of the system with WhatPulse.
WhatPulse is a simple program and gets downloaded and installed in your system in real time. Just click on the program icon on your desktop and see how many clicks you can make in a period of time.
The ‘Settings’ option allows you to make the program run at Windows Startup, check for new versions automatically, enable portable mode, hide pop-ups and much more.
I didn’t notice any errors while testing the programs and it worked smoothly on my Windows 8.1, giving me the accurate details about my computing habits. It landed on my system in real time and didn’t affect my system’s performance.
Overall WhatPulse is a nice and reliable program which tracks and records the details of your computing habits along with the statistics like IP address, downloading/uploading speed, network interface, total number of reboot sessions, bandwidth usage and application usage.
Track Your Computer Activity
WhatPulse is a free key-counting program which monitors your computer uptime, the number of keystrokes, bandwidth usage and the number of mouse clicks over a period of time. WhatPulse counts the number of times keys are pressed unlike the other keyloggers which record the order in which the keys are pressed. It also keeps the detailed history of how much work you’ve done on your computer system in a set period of time.WhatPulse is a simple program and gets downloaded and installed in your system in real time. Just click on the program icon on your desktop and see how many clicks you can make in a period of time.
What Does WhatPule Do
WhatPulse for Windows doe the following:- Tracks
your clicks – The software maps your mouse usage and keeps a track of
your clicks. It also let you export or share your mouse heat map.
- Tracks
Internet Usage- The program tracks your internet usage and also
discovers what all applications are making your internet slow by eating
up your bandwidth.
- Tracks
your keyboard usage- It maps your keyboard usage and keeps a track of
the keys you have pressed. You can also share your heat map with your
friends using WhatPulse.
- Monitors your network- Checks the application intensity and also monitors your concurrent incoming and outgoing network traffic.
- Application Usage- WhatPulse also keeps a track of most used applications by you.
The ‘Settings’ option allows you to make the program run at Windows Startup, check for new versions automatically, enable portable mode, hide pop-ups and much more.
I didn’t notice any errors while testing the programs and it worked smoothly on my Windows 8.1, giving me the accurate details about my computing habits. It landed on my system in real time and didn’t affect my system’s performance.
Overall WhatPulse is a nice and reliable program which tracks and records the details of your computing habits along with the statistics like IP address, downloading/uploading speed, network interface, total number of reboot sessions, bandwidth usage and application usage.
WhatPulse free download
You can download the program here and track your computer activity.Monday, 25 August 2014
Friends of Technology: What is a Botnet attack and how does it work on a ...
Friends of Technology: What is a Botnet attack and how does it work on a ...: Botnets are networks of compromised computers, controlled by remote attackers in order to perform such illicit tasks as sending spam...
What is a Botnet attack and how does it work on a computer
Botnets
are networks of compromised computers, controlled by remote attackers
in order to perform such illicit tasks as sending spam or attacking
other computers. The word Bot comes from the word Robot and is referred
to any software program that carries out automated pre-defined tasks.
They can perform useful tasks as well as malicious tasks. Webmasters may
be familiar with the Google bot or the Bing bot that looks for an
crawls fresh content on the Internet.
What is a Botnet
Each computer in the Botnet is called a Node and they could be any computer, anywhere in the world – even yours, if an attacker has managed to surreptitiously install malware on your computer, by exploiting vulnerabilities in your operating system or installed software, or by tricking you into installing it. Such Nodes are then used to spread malware further, send spam mail or even attack other computers. Such Botnets are controlled en masse via protocols such as IRC. Some of you may want to learn more about Botnets.
Microsoft Malware Protection Center defines botnet as a network of computers that can be illicitly and secretly controlled at will by an attacker and commanded to take a variety of actions. Under this definition, a trojan downloader that is only designed to download arbitrary files and cannot otherwise be controlled by the attacker would not be considered a bot.
Botnets should be of concern to governments and businesses because of their ability to harness large numbers of individual computers to direct an attack against information technology infrastructure.
Microsoft
is taking an aggressive approach to fighting botnets by collaborating
with governments and others to take them down. Microsoft is also
providing businesses, governments, and consumers with security tools and
guidance. Working towards this goal, Microsoft has released a document
titled Botnets: Guidance for Governments, which can be downloaded at Microsoft.
Infographic
McAfee
has created a nice easy-to-understand Infographic explaining, what are
botnets. With the rapid growth in malware and bot infections all around,
it becomes important for all to understand what Botnets are and what
Zombies are.
This
Infographic nails the botnet lifecycle and economics just right… not
too technical, not too simple. Click on it to see the larger image.
Friends of Technology: Excessively loud fan, constant overheating issues ...
Friends of Technology: Excessively loud fan, constant overheating issues ...: It seems that even after 3 firmware patches in a month the bug that has been troubling some Surface Pro 3 users still remains unre...
Excessively loud fan, constant overheating issues plaguing some Surface Pro 3 i7 users
Expressing his disappointment, Jarem says that even after 3 replacements the tablet still continues to pose problems. The tablet’s fan is quote loud, coupled with unusual hotness, he mentions,
“After dropping over $2k on a product, this isn’t what I expect to see after 3 minutes of light web browsing. Not very happy at the moment as you can guess. I’m assuming that, with a working unit, you’re not supposed to even hear the fan under normal usage. Right out of the box, before & after all updates and firmware are installed : the back of the unit becomes uncomfortably hot and its fan spins very loudly on idle and while performing minor tasks such as web browsing (even sites without flash or heavy ad use)”.Jarem further says,
“I was surprised to hear it the first time, as it sounds like white noise coming from the right speaker. Even under its idle state, my Surface Pro 3 is currently the loudest thing in my office (and that’s including my PC running 3 video cards SLI). At its peak (IE: high octane tasks like browsing slashdot.com and reading OneNote entries), the fan noise is ear-piercing and the heat produced is immensely hot. I mean, it’s not something you’d want to hold, immense”.The problem appears to be happening with the i7 models of Surface Pro 3 tablets. No matter what application is being run on the tablet whether it is games, browsing or videos the problem is happening randomly. Several other users of Surface Pro 3 i7 also raised this issue in that post.
Getting the faulty Tablet replaced at a Microsoft store is recommended, however another firmware update for the Surface Pro 3 looks imminent.
Saturday, 23 August 2014
Friends of Technology: USBDriveFresher: Junk file and folder cleaner for ...
Friends of Technology: USBDriveFresher: Junk file and folder cleaner for ...: We are aware of several disk cleaners like CCleaner , which many of us use frequently to clear our Windows PC of the junk files which ...
USBDriveFresher: Junk file and folder cleaner for USB Drives
We are aware of several disk cleaners like CCleaner,
which many of us use frequently to clear our Windows PC of the junk
files which the operating system creates over a period of time. Today,
we bring to you a free junk cleaner for your USB Drive.
Some instances of these files and folders include ._* files, .Trashes folder, .Spotlight-V100, .ds_store or even the thumbs.db files.
This tool will help you identify and delete the junk files and folders on your USB Drives. You can set up the cleanup rules by selecting which files you want to be deleted. You can also add your own file-types, should you wish to do so.
If you want to auto-clean any USB pen drive as soon as you connect it, simply check the appropriate option.
Once done, you can choose to clean one or all of the connected removable media or go in for a custom clean up.

The key features of USBDriveFresher are:
Over the next 2 days, we will be high-lighting a couple of more such useful utilities for your USB Drives or removable storage. So stay tuned!
Meanwhile, you may also want to have a look at these free useful tools for your USB Drive:
Free junk cleaner for USB Drive
USBDriveFresher is a small freeware that will help you keep your USB Drive or Removable Media clean at all times. The Windows operating system and some programs that you may run, place some files or folders automatically on your USB drive. While they are important at that point of time, they may lose their usefulness later.Some instances of these files and folders include ._* files, .Trashes folder, .Spotlight-V100, .ds_store or even the thumbs.db files.
This tool will help you identify and delete the junk files and folders on your USB Drives. You can set up the cleanup rules by selecting which files you want to be deleted. You can also add your own file-types, should you wish to do so.
If you want to auto-clean any USB pen drive as soon as you connect it, simply check the appropriate option.
Once done, you can choose to clean one or all of the connected removable media or go in for a custom clean up.
The key features of USBDriveFresher are:
- Customizable cleanup patterns
- Predefined patterns
- Cleanup USB drive with a mouse click
- Auto-cleanup USB drive when it is plugged in
- Folder cleanup
Over the next 2 days, we will be high-lighting a couple of more such useful utilities for your USB Drives or removable storage. So stay tuned!
Meanwhile, you may also want to have a look at these free useful tools for your USB Drive:
- Desktop Media: Automatically adds and removes shortcut to USB drive on Desktop
- RemoveDrive: A free command-line tool to safely remove USB devices
- NetWrix’s USB Blocker: Prevent unauthorized use of USB and other removable media
- Dropout: A portable search tool for USB drives and Dropbox folder.
Friday, 22 August 2014
Friends of Technology: Incidence and usage of rogue antivirus software dr...
Friends of Technology: Incidence and usage of rogue antivirus software dr...: Rogue antivirus software is a malware that pretends (and acts) like an antivirus software. However, in reality it simply downloads ...
Incidence and usage of rogue antivirus software dropping
Rogue
antivirus software is a malware that pretends (and acts) like an
antivirus software. However, in reality it simply downloads malicious
software on your system and displays false detections of viruses on the
computer. After displaying this, the rogue antivirus software scares and
convinces users into paying fees to clean these ‘detections’. With such
tactics to trap users, rogue softwares have been an indivisible part of
malware ecosystem. Some of such fraud antivirus softwares are the Win32/FakeRean and Win32/SpySheriff that are active since 2007 and still making revenue.
However, Microsoft’s Malware Protection Center’s recent study shows that the usage of the rogue antivirus software is dropping significantly. The graph below is the result of this study that shows the overall trend of rogue antivirus software family for last one year (Aug’13 to Aug ’14).

As can be seen in the graph, the usage of the rogue antivirus software family, such as Win32/FakePAV, Win32/OneScan, Win32/FakeXPA and Win32/Winwebsec has gone significantly low in the year 2014.
It’s pretty surprising to see the trend going lower and lower. But Microsoft states the reason behind this downfall:
Rogue software always use different name combinations and brandings to hide their tracks and avoid detections by genuine antivirus programs. However the recent updates in antivirus programs, this covering is not working anymore. Hence, now-a-days, the rogue softwares are using other tricks to catch users’ attention towards them. Microsoft mentions that,
However, Microsoft’s Malware Protection Center’s recent study shows that the usage of the rogue antivirus software is dropping significantly. The graph below is the result of this study that shows the overall trend of rogue antivirus software family for last one year (Aug’13 to Aug ’14).
As can be seen in the graph, the usage of the rogue antivirus software family, such as Win32/FakePAV, Win32/OneScan, Win32/FakeXPA and Win32/Winwebsec has gone significantly low in the year 2014.
It’s pretty surprising to see the trend going lower and lower. But Microsoft states the reason behind this downfall:
“It’s likely this has happened due to the antimalware industry’s intense targeting of these rogues in our products, and better end-user awareness and security practices. In particular, greater education about the social engineering technique the rogues use, and the large number of legitimate, free antivirus products available on the market appear to have had an impact on a user’s willingness to pay for such pests.”So, actually, the free-of-cost availability of genuine antivirus software in the market has been the major driving force behind the drop of incidences of rogue antivirus software.
Rogue software always use different name combinations and brandings to hide their tracks and avoid detections by genuine antivirus programs. However the recent updates in antivirus programs, this covering is not working anymore. Hence, now-a-days, the rogue softwares are using other tricks to catch users’ attention towards them. Microsoft mentions that,
“In the past we’ve regularly seen rogues use the hosts file to block access to a legitimate security product’s websites to deny users protection against the threat…Rogue Win32/Defru has a different and simpler approach on how to trick the user and monetize on it. Basically, it prevents the user from using the Internet by showing a fake scan when using different websites.”At the ending note, Microsoft mentions that there are genuine, reliable yet free security programs such as Microsoft Security Essentials. Users should always do a thorough investigation about the authenticity of the antivirus program that asks you to pay for it.
Thursday, 21 August 2014
Friends of Technology: Windows 8 tablet may still enter Connected Standby...
Friends of Technology: Windows 8 tablet may still enter Connected Standby...: If you are using a Windows 8 tablet or a Windows RT based device and you have configured the Power Options to Turn Off Display when P...
Windows 8 tablet may still enter Connected Standby, even when you disable Turn Off Display
If you are using a Windows 8 tablet or a Windows RT based device and you have configured the Power Options to Turn Off Display when Plugged in, to Never, then Windows may be still able to enter the Connected Standby
power state and turn off display. Microsoft has described this scenario
in a Windows 8 tablet, and offered an explanation for why it happens
so.

Why does this happen?
KB2854058 explains that this behavior is by design.
When the machine is idle and with AC plugged in, Windows may trigger Automatic Maintenance, if it is due. During this scheduled maintenance task, winsat.exe get triggered to perform some jobs and carry out certain performance evaluation. In such scenarios, to get the work done fast and to get the accurate Windows Experience Index, winsat.exe will change the current power scheme for Highest Performance.
When this happens, the change of power scheme will change the Turn Off Display setting, to anything else, other than Never. This can trigger Connected Standby, in some cases.
If you set Turn Off Display Power Option to Never, Windows 8 or RT tablet could still enter Connected Standby
In this scenario, where your system is plugged in, idle and not doing any work you may find that Windows can enter Connected Standby, when you have set Turn Off Display Power Option to Never. In spite of this, the tablet will still enter the Connected Standby state and turn off display.Why does this happen?
KB2854058 explains that this behavior is by design.
When the machine is idle and with AC plugged in, Windows may trigger Automatic Maintenance, if it is due. During this scheduled maintenance task, winsat.exe get triggered to perform some jobs and carry out certain performance evaluation. In such scenarios, to get the work done fast and to get the accurate Windows Experience Index, winsat.exe will change the current power scheme for Highest Performance.
When this happens, the change of power scheme will change the Turn Off Display setting, to anything else, other than Never. This can trigger Connected Standby, in some cases.
Friends of Technology: Block Unwanted Calls and SMS on Windows Phone 8.1 ...
Friends of Technology: Block Unwanted Calls and SMS on Windows Phone 8.1 ...: One of life’s greatest annoyances are unwanted telemarketing calls that interrupt your sleep on Sunday morning or spoil evening dinne...
Block Unwanted Calls and SMS on Windows Phone 8.1 via Call + SMS Filter
One
of life’s greatest annoyances are unwanted telemarketing calls that
interrupt your sleep on Sunday morning or spoil evening dinner. Well,
you are not alone. Records suggest the number of unsolicited telephone
marketing calls and playing of automated or prerecorded messages to
mobile users have been on rise. As such, stopping live marketing calls
from telecom companies whose service you never subscribed or had
subscribed at one point but are no longer interested in continuing can
be a pain, especially when you fall short of necessary information in
this regard.
Features of Call + SMS filter:
 Under ‘Settings’ menu, scroll down to locate Call+SMS Filter option.
Under ‘Settings’ menu, scroll down to locate Call+SMS Filter option.
Next, accept the terms and conditions to go further with the blocking process. Move to the next step. A new menu should appear on your phone screen where you can notice Block numbers option.

Tap the option, select numbers from the recent call history and long tap the desired number. Here, different options would be listed. Choose Block option from the list and you’re done! Your chosen number is blocked out.
 You can download and install it manually from the Windows Phone Store. Are you a Windows Phone user? Let us know if it works for you.
You can download and install it manually from the Windows Phone Store. Are you a Windows Phone user? Let us know if it works for you.
Block Unwanted Calls or SMS on Windows Phone
Fortunately, Windows Phone 8.1 users have a solution at hand. They can block unwanted incoming calls and SMS via a new setting called Call + SMS Filter. The invaluable setting blocks unwanted calls and SMS. It is easy to set up, straightforward to use and integrates seamlessly with your call history and messaging. The app is new to Windows Phone and is designed by Nokia, exclusively for Nokia Lumia phones.Features of Call + SMS filter:
- Block incoming calls and SMS based on your own blocked numbers list.
- Add blocked numbers from Call History and Messaging
- Display the number of blocked calls and SMS from a Live Tile
Next, accept the terms and conditions to go further with the blocking process. Move to the next step. A new menu should appear on your phone screen where you can notice Block numbers option.
Tap the option, select numbers from the recent call history and long tap the desired number. Here, different options would be listed. Choose Block option from the list and you’re done! Your chosen number is blocked out.
Friends of Technology: LastPass Password Manager Review
Friends of Technology: LastPass Password Manager Review: With LastPasssPassword Manager, you have to remember only one password and it is the master password to access your password vault. T...
LastPass Password Manager Review
With LastPasssPassword Manager,
you have to remember only one password and it is the master password to
access your password vault. That is why they advertise it as “Last
password you have to remember”, you got your answer that you’ll have to
remember only the master password while Lastpass takes care of all your
other passwords and even forms. This review of Lastpass password manager
for Windows, will tell you if you can trust it and use it.

It took a whole lot of months for me to decide to go for a password manager. Prior to that, I was storing all my passwords in an excel sheet that was renamed to look as a garbage document with no extension. Whenever I forgot password for any particular site (I was not using hard passwords at that time), I changed the extension and opened it in Microsoft Excel. But I was still afraid that someone might figure it out and all my data would be stolen.
I needed a free password manager so I went through the available options. The first one I used was a desktop version and I had to enter master password every time I had to login into any of the web services. Plus the fear of getting hacked and unknown people using my login data was too much for me to keep using the desktop password manager application. I researched a bit and found Lastpass, a cloud based solution.
Cloud Based Password Manager

Being a cloud based password manager, I had the option of accessing it from anywhere and on any computer in the world. I just had to remember my email ID and Lastpass master password to use it from other computers. This looked perfect so I went with it, with fears about the security lapses it might be having. What if somebody hooked up to Lastpass servers? But then, it is possible that someone can hack any site and steal the credentials. It is happening with many sites – LinkedIn, Yahoo and even Amazon!
It is a risk but it still makes your daily computing, much easier. You get stronger passwords and you don’t have to remember them. There are some problems too – which we will discuss in a while. As a cloud based free password manager, Lastpass is good – if not perfect. Speaking of perfect, nothing is 100% perfect when it comes to the Internet. Hackers keep on trying with different techniques and there is always a possibility of security breach that can reveal all you data to bad guys. What security measures does Lastpass take, then, to avoid being compromised? Let us check them out in the next section.
Security in LastPass Password Manager
Lastpass claims that no one knows your master password as it is not stored “as is” anywhere. It is hashed and the value of hash is stored so that Lastpass knows that you have stored the correct password. I do not know if any other word or combination can provide same hash (in which case, storing only hash is not much fruitful as others with similar has can access your vault). I invite you to comment on whether two different passwords/passphrases can result into same hash.
Lastpass claims it uses AES 256 bit encryption to store your other passwords in cloud. In their own words,
You have to remember. Nothing is 100% secure! A few years back, the LastPass website had faced a security breach. Then again, last year, a bug in LastPass’s Internet Explorer plug-in had exposed passwords of some users.
Features of LastPass
Before I talk of Lastpass features, let me inform you that there are both free and paid versions of Lastpass. In this article, we are talking only about the free version of Lastpass, the cloud based password manager.
The feature I like the most is the password capture. When you sign up with a new website, Lastpass prompts you to ask if you wish to save that password. If you say yes, you will get a dialog box to save the credentials and whether to autofill or autologin. If you have more than one account for a website, you can still store passwords separately on Lastpass. In other words, it supports multiple accounts for almost all kinds of websites. That helps a lot but make sure you do not select “autologin” (when saving password) as it will not give you a chance to select what credentials to use. If you already selected autologin and are not able to use other accounts, you can open Lastpass Vault and uncheck autologin.
Another feature is that it can capture entire process of signing in. For banks and similar institutions, the login process are bit different. Lastpass allows you to capture all the sign in process so that you can auto login there too. Once you have the Lastpass account, I recommend you view the Tutorials so that you know what all you can do to make your sign in easier.
Lastpass also has password generator. It auto detects when you are creating password and offers you suggestions if you go for it. The new passwords can be customized with symbols and numbers and you can also set a size for them. The best part is, once you have saved it, you do not need to remember it!
Finally, Lastpass lets you import your passwords from other password managers. It supports a variety of formats so that you do not have to manually transfer data. Simply select import and select the file from other password managers and all data will be imported without human intervention. Similarly, Lastpass also allows export of data just in case you wish to move to some other password manager like RoboForm etc.
Problems With LastPass
I did not find any problems with Lastpass except that some sites create problem while auto-signing in. Some sites have captcha and there, you have to close the Lastpass dialog after it fills the password. After closing the Lastpass dialog, you can manually enter captcha. Since the captcha changes every time you login, I do not think there could be any way to capture such logins.
Lastpass support is readily available on Twitter. Their handle is @Lastpass and they offer fast response. The above review of Lastpass is meant as a support in choosing a cloud based password manager for you. If you have any thoughts, please share.
LastPass review
It took a whole lot of months for me to decide to go for a password manager. Prior to that, I was storing all my passwords in an excel sheet that was renamed to look as a garbage document with no extension. Whenever I forgot password for any particular site (I was not using hard passwords at that time), I changed the extension and opened it in Microsoft Excel. But I was still afraid that someone might figure it out and all my data would be stolen.
I needed a free password manager so I went through the available options. The first one I used was a desktop version and I had to enter master password every time I had to login into any of the web services. Plus the fear of getting hacked and unknown people using my login data was too much for me to keep using the desktop password manager application. I researched a bit and found Lastpass, a cloud based solution.
Cloud Based Password Manager
Being a cloud based password manager, I had the option of accessing it from anywhere and on any computer in the world. I just had to remember my email ID and Lastpass master password to use it from other computers. This looked perfect so I went with it, with fears about the security lapses it might be having. What if somebody hooked up to Lastpass servers? But then, it is possible that someone can hack any site and steal the credentials. It is happening with many sites – LinkedIn, Yahoo and even Amazon!
It is a risk but it still makes your daily computing, much easier. You get stronger passwords and you don’t have to remember them. There are some problems too – which we will discuss in a while. As a cloud based free password manager, Lastpass is good – if not perfect. Speaking of perfect, nothing is 100% perfect when it comes to the Internet. Hackers keep on trying with different techniques and there is always a possibility of security breach that can reveal all you data to bad guys. What security measures does Lastpass take, then, to avoid being compromised? Let us check them out in the next section.
Security in LastPass Password Manager
Lastpass claims that no one knows your master password as it is not stored “as is” anywhere. It is hashed and the value of hash is stored so that Lastpass knows that you have stored the correct password. I do not know if any other word or combination can provide same hash (in which case, storing only hash is not much fruitful as others with similar has can access your vault). I invite you to comment on whether two different passwords/passphrases can result into same hash.
Lastpass claims it uses AES 256 bit encryption to store your other passwords in cloud. In their own words,
“We’ve taken every step we can think of to ensure your security and privacy. Using an evolved host-proof hosted solution, LastPass employs localized, government-level encryption (256-bit AES implemented in C++ and JavaScript) and local one-way salted hashes to give you complete security with the go-anywhere convenience of syncing through the cloud. All encrypting and decrypting happens on your computer – no one at LastPass can ever access your sensitive data.”I highlighted the last sentence above as it raises doubts that someone has to clear (preferably from Lastpass). If all encryption and decryption happens on my computer, does it make my password vault vulnerable by leaving traces of its actions?
You have to remember. Nothing is 100% secure! A few years back, the LastPass website had faced a security breach. Then again, last year, a bug in LastPass’s Internet Explorer plug-in had exposed passwords of some users.
Features of LastPass
Before I talk of Lastpass features, let me inform you that there are both free and paid versions of Lastpass. In this article, we are talking only about the free version of Lastpass, the cloud based password manager.
The feature I like the most is the password capture. When you sign up with a new website, Lastpass prompts you to ask if you wish to save that password. If you say yes, you will get a dialog box to save the credentials and whether to autofill or autologin. If you have more than one account for a website, you can still store passwords separately on Lastpass. In other words, it supports multiple accounts for almost all kinds of websites. That helps a lot but make sure you do not select “autologin” (when saving password) as it will not give you a chance to select what credentials to use. If you already selected autologin and are not able to use other accounts, you can open Lastpass Vault and uncheck autologin.
Another feature is that it can capture entire process of signing in. For banks and similar institutions, the login process are bit different. Lastpass allows you to capture all the sign in process so that you can auto login there too. Once you have the Lastpass account, I recommend you view the Tutorials so that you know what all you can do to make your sign in easier.
Lastpass also has password generator. It auto detects when you are creating password and offers you suggestions if you go for it. The new passwords can be customized with symbols and numbers and you can also set a size for them. The best part is, once you have saved it, you do not need to remember it!
Finally, Lastpass lets you import your passwords from other password managers. It supports a variety of formats so that you do not have to manually transfer data. Simply select import and select the file from other password managers and all data will be imported without human intervention. Similarly, Lastpass also allows export of data just in case you wish to move to some other password manager like RoboForm etc.
Problems With LastPass
I did not find any problems with Lastpass except that some sites create problem while auto-signing in. Some sites have captcha and there, you have to close the Lastpass dialog after it fills the password. After closing the Lastpass dialog, you can manually enter captcha. Since the captcha changes every time you login, I do not think there could be any way to capture such logins.
Lastpass support is readily available on Twitter. Their handle is @Lastpass and they offer fast response. The above review of Lastpass is meant as a support in choosing a cloud based password manager for you. If you have any thoughts, please share.
LastPass download
You can download LastPass from its official website.Wednesday, 20 August 2014
Friends of Technology: Bitdefender Total Security 2015 Review and Giveawa...
Friends of Technology: Bitdefender Total Security 2015 Review and Giveawa...: We’ve recommended Bitdefender Internet Security in the past and organized a giveaway too. This time, we are back with a Bitdefender Tota...
Bitdefender Total Security 2015 Review and Giveaway
We’ve recommended Bitdefender Internet Security in the past and organized a giveaway too. This time, we are back with a Bitdefender Total Security 2015
giveaway. If you are looking for a security software which can protect
your system as well as your social networking accounts from malware
attacks, read this review and participate in the giveaway, if you want a
free license.

Bitdefender Total Security 2015 software defends your PC against all types of malware, including: Computer viruses, Worms, Trojan viruses, Rootkits, Bots, Spyware and much more. Bitdefender Antivirus is one of the top-performing security suites that has improved over the time by protecting your computer systems from various threats.
Bitdefender Total Security 2015 brings the same perfect protection for your system with a strong range of new features and some new profile settings. It offers the active virus control and also monitors your computer’s behaviour regularly so that you can prevent the attacks of malicious codes in your system.
Unlike the other security programs Bitdefender Total Security 2015 has only essential security tools and it does quite a good job. Along with its antivirus security and firewall settings, Bitdefender also offers a Facebook scanner and parental controls.
Its ‘Quick scans’ can check the hidden locations of your system, such as Windows directory and Program Files. Additional scan options of the program focus on the file types and types of objects to target like memory, boot sectors, registry, rootkits and cookies. You can also schedule the custom scans for specific files or directories.
The main overview of Bitdefender is the same with a modern feel and a clean interface. A streamlined interface and systematically categories options make it a user friends security system.
New Features of Bitdefender Total Security 2015.


Overall Bitdefender Total Security provides an impeccable security to your computer systems against phishing, virus attacks, hacking attempts and various other threats. It has its own firewall configuration which turns ON automatically during installation. Additional it sends a weekly report including all your security stats. The tool is completely stealthy and lands on your PC without any issues. It worked great on my Windows 8.1!
Giveaway
In association with Bitdefender, we’re giving away 10 license keys for Bitdefender Total Security 2015 which normally costs $59.95 (1 year for 1 PC) free. All you have to do is share this post on any social networking site of your choice, and share its status URL here.
The giveaway will close after 10 days, We will select the winners names after 10 days and announce their names here in the comments section of this post. Please make sure your email ID is visible, linked to your name/profile – else you may post it in the comments itself.
Incidentally, BitDefender also offers several free tools for Windows, you may want to have a look at!
Bitdefender Total Security 2015 review
Bitdefender Total Security 2015 software defends your PC against all types of malware, including: Computer viruses, Worms, Trojan viruses, Rootkits, Bots, Spyware and much more. Bitdefender Antivirus is one of the top-performing security suites that has improved over the time by protecting your computer systems from various threats.
Bitdefender Total Security 2015 brings the same perfect protection for your system with a strong range of new features and some new profile settings. It offers the active virus control and also monitors your computer’s behaviour regularly so that you can prevent the attacks of malicious codes in your system.
Unlike the other security programs Bitdefender Total Security 2015 has only essential security tools and it does quite a good job. Along with its antivirus security and firewall settings, Bitdefender also offers a Facebook scanner and parental controls.
Its ‘Quick scans’ can check the hidden locations of your system, such as Windows directory and Program Files. Additional scan options of the program focus on the file types and types of objects to target like memory, boot sectors, registry, rootkits and cookies. You can also schedule the custom scans for specific files or directories.
The main overview of Bitdefender is the same with a modern feel and a clean interface. A streamlined interface and systematically categories options make it a user friends security system.
New Features of Bitdefender Total Security 2015.
- StartUp Optimizer
– This tool allows you to disable or delay any app from your from your
StartUp, thereby helping you to increase Windows startup speed.
- OneClick Optimizer- This tool frees up the space in your system by removes unnecessary files.
- PC CleanUP Wizard- This feature helps users to clean up the browser cache, Windows junk files, memory dumps in the system and error reporting files.
- Disk Fragmenter – It allows you to reduce fragments in specific drives which ensures a smoother computer performance.
- Registry Cleaner- This tool helps you to clean specific areas in your computer system.
- Duplicate File Remover-As the name suggests, this tool detects the duplicate files in your system and removes them creating more of free space.
- Besides its virus detection capabilities, Bitdefender also brings parental control, antispam and social network protection.
Overall Bitdefender Total Security provides an impeccable security to your computer systems against phishing, virus attacks, hacking attempts and various other threats. It has its own firewall configuration which turns ON automatically during installation. Additional it sends a weekly report including all your security stats. The tool is completely stealthy and lands on your PC without any issues. It worked great on my Windows 8.1!
Giveaway
In association with Bitdefender, we’re giving away 10 license keys for Bitdefender Total Security 2015 which normally costs $59.95 (1 year for 1 PC) free. All you have to do is share this post on any social networking site of your choice, and share its status URL here.
The giveaway will close after 10 days, We will select the winners names after 10 days and announce their names here in the comments section of this post. Please make sure your email ID is visible, linked to your name/profile – else you may post it in the comments itself.
Incidentally, BitDefender also offers several free tools for Windows, you may want to have a look at!
Friends of Technology: Browser Security Tests to check if your Browser is...
Friends of Technology: Browser Security Tests to check if your Browser is...: There are a number of things that make up a browser. It is not just about surfing the Internet, but surfing it safely. Security is one...
Browser Security Tests to check if your Browser is secure
There
are a number of things that make up a browser. It is not just about
surfing the Internet, but surfing it safely. Security is one of the most
important aspects of any browser, and you need to know if your browser
offers you enough protection. There are many aspects to browsing that
you need to know exist and that your browser does not compromise on
security to let you surf the Internet.

Browserscope.org is a website that offers a number of tests to determine the security of your browser. In addition to security, it also hosts a number of tests to let you know how it deals with scripts etc. The names of tests are listed on the upper tab.
Click on “About” under each test to see the number of tests and what the tests do. Click on “Results” to view results of previous tests run by other users. Click on “Tests” to run the tests on your own browser. You can choose to share the results of your test with others by selecting “Share” on the “Tests” page.

When you are browsing on the Internet, your browser leaves digital footprints. This allows other websites to gather information about you. This includes the applications installed on your computer and your surfing activity.
To know what all information your browser shares with other websites, log on – using the browser – to browserspy.dk. There are some 64+ tests available that let you know all the information your browser shares with the websites you visit.

PCFlank.com offers a number of tests that allow you to test your computer firewall, browser and more. Since we are talking about the browsers in this article, PCFlank does a good job in finding out what all information does your browser share with websites you are visiting. If any vulnerability is found, PCFlank will recommend steps to fix the problem(s).

BrowserCheck shows you the browser you are using and gives you two options – 1) run a quick scan or 2) install a plug-in – to know if the browser has any security issues. In my case, I found three issues when performing the test with Google Chrome 18.0.1025.162. Check the image to see the issues and the recommendations I got from BrowserCheck.

Panopticlick is another website that will check if your browser’s configuration is unique and then give you a uniqueness score. The more rare or unique your browser configuration, the less other websites will be able to track you, even if you limit or disable cookies.
These are some websites I know that answer the question – Is my browser safe. If you know of any other website or have a favorite, do share with us – and yes, let us know how your browser performed!
Is my Browser secure?
If you are wondering if your browser is secure, here are some websites that are designed to test browsers. You can simply visit these websites and see where your browser stands in terms of security. Some of these websites allow you to share and thereby compare data gathered by running tests on two or more browsers.BrowserScope
Browserscope.org is a website that offers a number of tests to determine the security of your browser. In addition to security, it also hosts a number of tests to let you know how it deals with scripts etc. The names of tests are listed on the upper tab.
Click on “About” under each test to see the number of tests and what the tests do. Click on “Results” to view results of previous tests run by other users. Click on “Tests” to run the tests on your own browser. You can choose to share the results of your test with others by selecting “Share” on the “Tests” page.
BrowserSpy
When you are browsing on the Internet, your browser leaves digital footprints. This allows other websites to gather information about you. This includes the applications installed on your computer and your surfing activity.
To know what all information your browser shares with other websites, log on – using the browser – to browserspy.dk. There are some 64+ tests available that let you know all the information your browser shares with the websites you visit.
PCFlank
PCFlank.com offers a number of tests that allow you to test your computer firewall, browser and more. Since we are talking about the browsers in this article, PCFlank does a good job in finding out what all information does your browser share with websites you are visiting. If any vulnerability is found, PCFlank will recommend steps to fix the problem(s).
Qualys BrowserCheck
BrowserCheck shows you the browser you are using and gives you two options – 1) run a quick scan or 2) install a plug-in – to know if the browser has any security issues. In my case, I found three issues when performing the test with Google Chrome 18.0.1025.162. Check the image to see the issues and the recommendations I got from BrowserCheck.
Panopticlick
Panopticlick is another website that will check if your browser’s configuration is unique and then give you a uniqueness score. The more rare or unique your browser configuration, the less other websites will be able to track you, even if you limit or disable cookies.
These are some websites I know that answer the question – Is my browser safe. If you know of any other website or have a favorite, do share with us – and yes, let us know how your browser performed!
Friends of Technology: Hide local disk drive without using any third part...
Friends of Technology: Hide local disk drive without using any third part...: Nowadays, Most of the PC users have personalized data that he/she wants to hide from other users of that system.There are lot of f...
Hide local disk drive without using any third party application
Nowadays, Most of the PC users have personalized data that he/she wants
to hide from other users of that system.There are lot of freewares or
paid third party applications are available over the internet, but what
if there is no internet connection available also no application is
available at that time? Straight forward answer is to hide partitions
from displaying them from My Computer section!
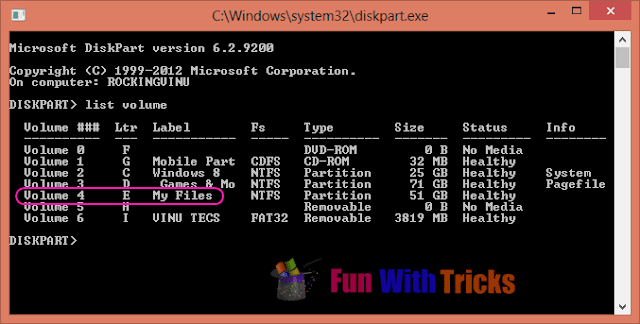
2. You will get command prompt like window. Just type "list volume" in from of "DISKPART>" and hit Enter. You will get list of volumes available on your system with their drive letters. Make note of volume number and drive letter from the list which you want to hide. In my case volume number is 4 and drive letter is E.
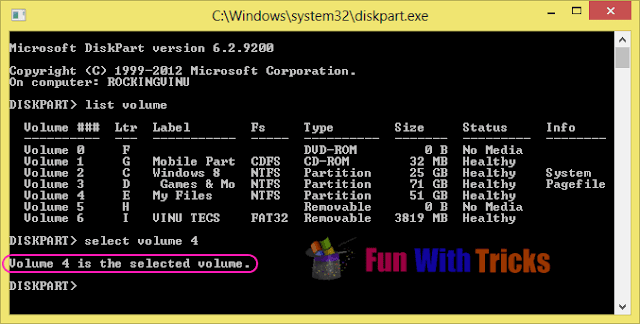
3. Enter command as "select volume volume_no". Replace volume_no with the volume number of the drive you want to hide. In my case, the command looks like "select volume 4". If everything is all right then you will get message as "Volume xx is selected volume".
4. It's time to hide volume, Just enter command as "remove letter drive_letter". Replace drive_letter with drive letter from list which you want to hide. In my case the command becomes "remove letter E". You will get success message if all goes well.
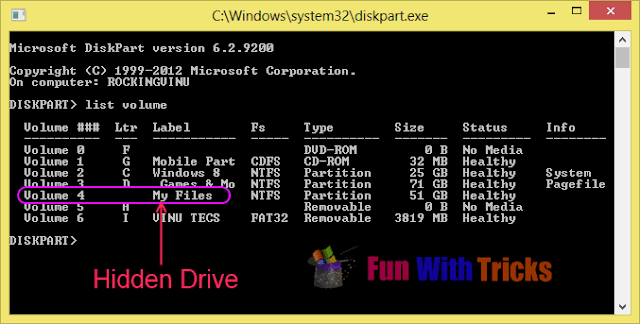
5. Now, check out whether drive is hidden or not!
2. Type "list volume" in from of "DISKPART>" and hit Enter. You will get list of volumes available on your system with their drive letter.If you have any hidden drives then the letter will not be displayed on disk. Make note of the volume number from list which you want to unhide.
3. Enter command as "select volume volume_no". Replace volume_no with your volume number from the list. In my case, the command looks "select volume 4". If all goes well, you will get message as "Volume xx is selected volume".
4. Enter command as "assign letter drive_letter". Replace drive_letter with the any letter that you want to assign to drive (Not necessary same as that of previous one).
5. Verify whether drive is now visible or not!
You can use this tutorial to assign drive letters manually.
Hide local disk drive without using any third party application
Steps you have to perform
I have 3 partitions on my system. From these, I am going to hide drive E from My Computer section! So lets start now!To hide the partition
1. Open Start->Run box. Type "diskpart" in text-field and hit enter.2. You will get command prompt like window. Just type "list volume" in from of "DISKPART>" and hit Enter. You will get list of volumes available on your system with their drive letters. Make note of volume number and drive letter from the list which you want to hide. In my case volume number is 4 and drive letter is E.
3. Enter command as "select volume volume_no". Replace volume_no with the volume number of the drive you want to hide. In my case, the command looks like "select volume 4". If everything is all right then you will get message as "Volume xx is selected volume".
4. It's time to hide volume, Just enter command as "remove letter drive_letter". Replace drive_letter with drive letter from list which you want to hide. In my case the command becomes "remove letter E". You will get success message if all goes well.
5. Now, check out whether drive is hidden or not!
To un-hide the partition
1. Open same diskpart utility as we opened in step 1 to hide the partition.2. Type "list volume" in from of "DISKPART>" and hit Enter. You will get list of volumes available on your system with their drive letter.If you have any hidden drives then the letter will not be displayed on disk. Make note of the volume number from list which you want to unhide.
3. Enter command as "select volume volume_no". Replace volume_no with your volume number from the list. In my case, the command looks "select volume 4". If all goes well, you will get message as "Volume xx is selected volume".
4. Enter command as "assign letter drive_letter". Replace drive_letter with the any letter that you want to assign to drive (Not necessary same as that of previous one).
5. Verify whether drive is now visible or not!
You can use this tutorial to assign drive letters manually.
Tuesday, 19 August 2014
Friends of Technology: Remove or Uninstall Windows Updates in Windows 7 /...
Friends of Technology: Remove or Uninstall Windows Updates in Windows 7 /...: We all prefer to keep our Windows operating system updated. But sometimes some Windows Updates may make your PC go crazy. Maybe your ...
Remove or Uninstall Windows Updates in Windows 7 / 8
We
all prefer to keep our Windows operating system updated. But sometimes
some Windows Updates may make your PC go crazy. Maybe your Windows
computer has gone in a loop! In this post we will see how to remove or
uninstall Windows Updates and troubleshoot & fix problems caused due
to them in Windows 8 / 7.
If
you find yourself in one of these situation while dealing with Windows
Updates then try some of the solutions provided here. These are some of
the most common solution of most common problems. In some cases, you may have to enter the safe mode to be able to carry out the suggestions.
Uninstall Windows Updates
To remove a particular update do the following:
Updates
are meant to enhance the security of your computer, it’s best not to
remove an update unless you’re certain that it is causing a problem.
Take these steps to be certain you want to remove an update:
- In Windows 7, click Start and the click All Programs and select Windows Update from the list of programs. In Windows 8, open the WinX menu and click open Control Panel. Now open Windows Update applet.
- From the View update history,select the update that you want to remove, and note down its KB number. I suggest you go here first as it offers some description too.
Now open the Program and Features applet of the Control Panel, and from the left side click on View Installed Updates. Right-click on the Update you wish to uninstall and click on Uninstall. The update will get installed. You may be required to reboot you computer.
It is important to mention that if you have used the Disk Cleanup Tool to delete the Windows Update Cleanup option, then you might not be able to uninstall the Update.
Remove Windows Updates using command line
To uninstall Windows Updates using the command line, open an elevated command prompt window, type the following and hit Enter:wusa /uninstall /kb:1234567
Here
1234567 should be the number of the Update you wish to uninstall. Here
we are using the built-in WUSA or Windows Update Standalone Installer
tool.
TROUBLESHOOTING SCENARIOS AND TIPS
1. A recently installed update is causing problem:
If you are sure enough that recently installed update is causing the
problem then only try these steps or before uninstalling it try to find
information about any problems that have occurred on the computer by
checking for a solution. If no solutions are available, check the
Windows Update history to learn more about recently installed updates.
- Click Start and the click All Programs and select Windows Update from the list of programs.
- In the left pane, click View update history.
- To view more information about an update, double-click it.
2. You are not able to remove an update:
You may face this error because you might be connected to a network
where updates are managed by Group Policy. These network-wide settings
can prevent you from removing an update. In other cases, you might not
be able to remove an update because it applies to a security-related
area of the operating system. If you think an update that you can’t
remove is causing problems, contact system administrator of your
organization.
3. A removed update is getting reinstalled automatically:
Your computer is probably connected to a network where Group Policy
settings determine which updates must be installed on each computer.
These network-wide settings can reinstall any required updates that
you’ve removed.
You might also have
Windows set to automatically install updates, which is the recommended
setting for your computer. If you don’t want Windows to install an
update, you need to hide it.
- Click Start and the click All Programs and select Windows Update from the list of programs.
- In the left pane, click Check for updates.
- When Windows finds updates for your computer, do one of the following:
- Click on important updates links if you have important updates to hide.
- Click on optional updates links if you have optional updates to hide.
- Right-click the update you don’t want to install, and then click Hide update. The next time you check for updates, the update won’t be automatically selected or installed.
The
same steps are also applied if you want to stops Windows Updates
offering an update that you don’t want to install like Language packs.
4. Your Device or Hardware is not working after updating its device drivers from Windows Update:
You might need to revert to a previous version of the driver for that
device. Check the manufacturer’s website for a more recent version of
the driver, or remove the driver and restart your computer.
Monday, 18 August 2014
Friends of Technology: Freeware to fix or remove Broken Shortcuts in Wind...
Friends of Technology: Freeware to fix or remove Broken Shortcuts in Wind...: Having too many broken shortcuts on your Windows can be messy and its a good idea to scan for and remove broken shortcuts every once i...
Freeware to fix or remove Broken Shortcuts in Windows
Having
too many broken shortcuts on your Windows can be messy and its a good
idea to scan for and remove broken shortcuts every once in a while –
just a matter of good house-keeping! While most
Fix It to remove broken desktop shortcuts
 This Fix It from Microsoft will remove broken shortcuts. Specifically it will fix:
This Fix It from Microsoft will remove broken shortcuts. Specifically it will fix:
Bad Shortcut Killer

Bad Shortcut Killer is a freeware that will scan your Windows start menu, jump lists and desktop and fix or delete them easily. To fix the broken shortcuts, run Bad Shortcut Killer. Click on the ‘Find Bad Shortcuts’ button and the tool will search for invalid shortcuts. Once the scan is completed, you will be presented with a list of broken shortcuts.
Select the shortcuts that you think are broken and click on the ‘Delete Selected Shortcuts’ button. The broken or invalid shortcuts will be deleted. This freeware can do the following:
Broken Shortcut Fixer

Broken Shortcut Fixer scans your Windows computer for broken shortcuts and automatically repairs any shortcuts that it can find using the Windows link resolve method. To use this broken shortcut remover:
What are broken shortcuts
If you have deleted or uninstalled programs, deleted bookmarks, moved files or folders to another place, then once-valid shortcuts may point to now non-existent files. Such shortcuts are called bad or invalid or broken shortcuts, and you should remove them.Remove Broken Shortcuts
As I mentioned, having broken shortcuts on your desktop or start menu can be messy and irritating at times. Imagine clicking on a shortcut and receiving an error message and finding that it points nowhere! Here are a few tools that can help remove broken shortcuts in Windows.Fix It to remove broken desktop shortcuts
- Problems with desktop shortcuts and icons
- Shortcuts on the desktop don’t work or are broken
- Desktop icons are broken or have not been used in 3 months
- Startup items don’t work or are broken
Bad Shortcut Killer
Bad Shortcut Killer is a freeware that will scan your Windows start menu, jump lists and desktop and fix or delete them easily. To fix the broken shortcuts, run Bad Shortcut Killer. Click on the ‘Find Bad Shortcuts’ button and the tool will search for invalid shortcuts. Once the scan is completed, you will be presented with a list of broken shortcuts.
Select the shortcuts that you think are broken and click on the ‘Delete Selected Shortcuts’ button. The broken or invalid shortcuts will be deleted. This freeware can do the following:
- It searches Start Menu, Desktop, Jump Lists & Startup Folder for broken shortcuts.
- It can remove the invalid shortcuts
- It keep your start menu & desktop tidy and free from broken shortcuts
- Help keep invalid shortcuts off of your start menu and your desktop.
Broken Shortcut Fixer
Broken Shortcut Fixer scans your Windows computer for broken shortcuts and automatically repairs any shortcuts that it can find using the Windows link resolve method. To use this broken shortcut remover:
- Click “Scan Shortcuts” to repair and find broken shortcuts.
- Double-click broken shortcuts to view them in Windows.
- Hover over a broken shortcut to see the broken path.
- “Delete Broken Shortcuts” will send the selected shortcuts to the Recycle Bin.
Sunday, 17 August 2014
Friends of Technology: Find viruses using Windows netstat feature
Friends of Technology: Find viruses using Windows netstat feature: sometimes people want to know if they are infected by a RAT or something.We must have some alternatives to protect our private data ...
Find viruses using Windows netstat feature
sometimes people
want to know if they are infected by a RAT or something.We must have
some alternatives to protect our private data other than third party
software.This tutorial may help you to prevent such kinds of threats
from being your system unstable!
2. Check the PID (Process Identifier) checkbox .
3. Now, organize Task Manager by PID by clicking over PID from columns names as shown below. This will make things easier to read for the next step.
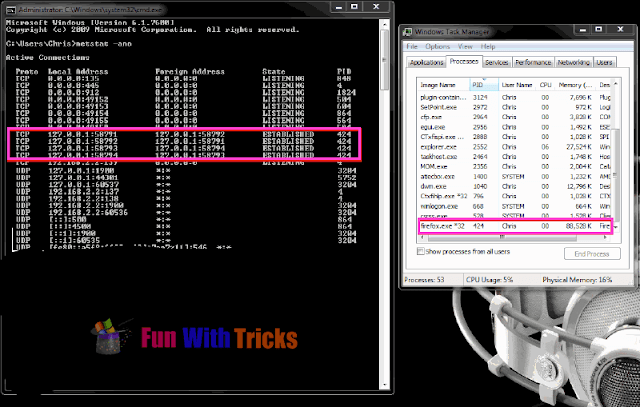
4. Open command prompt from start menu. Enter command as "netstat -ano". It will display all the processes which are listening or establishing connection to network.
Only look for ESTABLISHED connections (it would be established if its a RAT or malicious), read the PID and crosscheck into Task Manager. Notice in my example that the only established connections use the PID 424. Lets take a look at what that is:
As we can see, its Firefox. Now lets say you notice the PID reads something like "svchost.exe". You should open the file location by right clicking it and pressing Open File Location and either scan it with Virustotal or check to see if in its legit location (if it was in Appdata or Program Files and it is svchost.exe, then you may have a problem).
Find viruses using Windows netstat feature
Steps you have to perform
1. Open Task Manager (ctrl+alt+del OR ctrl+shift+esc). Go to the processes tab, click View from menu bar & click on Select Columns.3. Now, organize Task Manager by PID by clicking over PID from columns names as shown below. This will make things easier to read for the next step.
4. Open command prompt from start menu. Enter command as "netstat -ano". It will display all the processes which are listening or establishing connection to network.
Only look for ESTABLISHED connections (it would be established if its a RAT or malicious), read the PID and crosscheck into Task Manager. Notice in my example that the only established connections use the PID 424. Lets take a look at what that is:
As we can see, its Firefox. Now lets say you notice the PID reads something like "svchost.exe". You should open the file location by right clicking it and pressing Open File Location and either scan it with Virustotal or check to see if in its legit location (if it was in Appdata or Program Files and it is svchost.exe, then you may have a problem).
Saturday, 16 August 2014
Friends of Technology: Hide last name on Facebook [Working in 2014]
Friends of Technology: Hide last name on Facebook [Working in 2014]: You might see that some users have only first name as their name on Facebook timeline and even you tried to do that but Facebook...
Hide last name on Facebook [Working in 2014]
You might see that some users have only first name as their name on
Facebook timeline and even you tried to do that but Facebook doesn't
allow to show your first name as whole name unless and util you are an
Indonesian user. So how to show to Facebook system that you are an
Indonesian user even though you are not? You may think of using
Indonesian proxy, VPNs? Yes, you are bit close to the trick but now
Facebook have patched their loophole to disallow other users to pretend
as Indonesian user to set first name as complete name. Still as said
like nothing is impossible, their is a way to bypass their system. So
follow the steps to hide your last name on Facebook.
How to hide last name on Facebook?
Steps you have to perform
1. Log in to your Facebook account.2. Navigate to "Account Settings" page.
3. Change the language from "English" or any other language you set earlier to "Bahasa Indonesia". Click on "Save Changes".
4. Now you need to show Facebook system that you are actually from Indonesia. To do so, simply get any live Indonesian proxy from here.
5. Copy down proxy and it's port. Make sure the proxy have medium level speed and its of "Transparent"anonymity.
6. Now we need to set this proxy into browser. I have used "Mozilla Firefox" while doing this trick. So I have shown here screenshot to set proxy on Firefox browser. Do the similar with other browsers.
I have already a proxy in my browser! What should I do?
Don't worry, I have solution for this too. You need to register here and download the VPN software "PD- Proxy". Remember your username and password, you need to enter the credential into software.Note: Normal users who don't have proxy in browser should skip these steps! Continue with step 7.
- After downloading their software, extract it and open "PD-Proxy.exe". Wait until it installs network drivers.
- Fill your username and password in main window.
- Switch to settings tab. Click on "Show advance settings".
- Switch to "Parent proxy" section. Enter the proxy and port that your browser currently have. Click on "Save & go back". Make sure you have selected "Server and protocol" as "Demo server" and "TCP". Click on connect. You should get successful connected message.
- Remove proxy port from browser. Now follow below steps normally.
7. Select Tools -> Options -> Select "Advanced" tab -> Network -> Tick on "Manual proxy configuration" , write down your proxy and port address and tick on "Use this proxy for all protocols" -> Click on save.
Note: Do not use the proxy shown in screenshot, It may get dead. Always use fresh proxies.
8. It's time to hide your last name. Because we have changed the language to Indonesia, follow my screenshots to do necessary steps. Click on "Sunting" in front of "Nama". Fill your first name and clear all other fields. Enter your password and hit enter.
10. Revert back the proxy settings to default one. Change language back to "English (US)" or your one's.
Subscribe to:
Posts (Atom)